How hidden is your online activity, really? I’m not talking about the data that goes through your wire. I’m talking, your activity on social networks, your forum chat, your personal username, and your email address. This article talks about online footprint, and the methods used by experts, on how to remain quiet online…and how fruitless that can be.
The good old days…before reverse lookups.
There was a time when you had some control over your digital presence and security. You never felt insecure while sharing your personal details with someone. Why? Because you would know that this information was in safe hands and no one could invade your online life. But, evolving technology has altered it once and for all.
The darknet may have existed, hackers may have been around..but generally, online bad guys were not set out to find your online data.
The good & the bad got up-skilled

Every online platform has security and privacy settings. Your data today is shared with people and organisations all over the world. Organisations make a fortune, just from your data.
From creating a contact list to listening to music or playing games, you can’t do anything without revealing your personal information. Social media platforms are capable of predicting users’ activities and interests based on their previous behavior. Your friends’ activities and posts can tell a lot about your online life and personality. And this is just generally, good organisations.
The hackers who set out to steal your information can collect far more information than anyone organisation could collect (due to legal limitations).
What the Internet Savvy do..and how it can be useless
Shadow Profiles : hiding from reverse lookups
Your decision to delete a user profile doesn’t remove your digital presence. Your interactions, activities, and interests will keep you profiled on other user profiles that you interacted with. These alone can be used to follow your digital traces to plot your activity. This is what is known as a shadow profile.

It’s a dilemma. If you use the internet, there will be a shadow profile on you, multiple in fact. You may not be aware of it, or where they exist, but they are there. Facebook’s owner, now known as Meta, Mark Zuckerberg, also admitted that they collect details of people who don’t use their social platforms.
Accepted, deleting online profiles can hide you from reverse search engines such as our automated user search tool and email search tool. But, we can still determine if you ‘used’ to use those systems, we just don’t automate it. How? Simple, read our article here on how to find someone on social networks (even after they are deleted).
Who is your weakest ‘social media’ link?
Your weakest link. How many times, since you started using social networks, have you posted or commented on a friend’s comment or picture? What about the times you’ve forgotten that you actually did it?
The way you speak to friends, family, and coworkers on social networks can reveal a lot about you. You can pick up clues on location, sex, orientation, interests, hobbies, and who your closest relationships are.
Data from friends, family, and social circles (weakest links) can help analysts to extract private information. Deleting your profile from that social network doesn’t delete your old activity!

How does music make you feel?
Your musical preferences say a lot about your online life. Big Music Data has declared that around 44% of their users listen to their music during their waking hours. This omnipresence creates a singular opportunity for others to identify and evaluate seasonal and diurnal patterns among the listeners.

Music choices are another way of determining the listeners’ emotional states and moods. Since music shapes and reflects emotions, the majority of the listeners prefer energetic music during the daytime and relaxing tracks in the evening.
Ages and groups also play a huge role in music selection. Youngsters normally go for intense, hip-hop, pop, and rock music while Latin Americans prefer more stimulating music. These choices are different from Asians who prefer the relaxing genre.
The dating site, Ashley Madison, is one of the biggest examples of history that had shaken the entire world after billions of personal data was exposed. This website had non-public profiles and people would generally use fake emails. However, imagine the vast amounts of communication material available that could easily identify the individual source, even if fake profile data was used.
Anonymous social messaging apps, virtual cards, gift cards used by teens as well as millennials are collecting personal data on each use. It’s how they make their margins.
Although there are numerous laws and regulations by global legislators, there is still a lot they have to improve.
Geo-Location Apps can Also Find You!
Most mobile apps ping your location every now and then without you knowing. While this may be expected for Pokemon Go or navigation apps, why would digital bible apps or flashlights need the same details? Obviously, the collected data is shared with 3rd party advertisers or data extractors to pitch custom sales offers. Have you ever wondered why do you get discount deals or coupon codes for a product that you are soon going to make a purchase (but on a different website/app)? The answer is simple- this is the result of user profiling combined data and someone has sold your data to the advertiser, using algorithms to work out what you’re likely to buy next. All this is in the background, without you knowing.
Data Shared at the Governmental Level
Governmental agencies have no exception when it comes to personal data collection. Many governmental agencies, like NSA, can access your data even if overseas.
Anyone with the required algorithms can easily look up these massive databases. They can extract individual or group details, exhibiting certain behavioral patterns. However, government authorities extract this data for counterterrorism planning, operations and safeguards.
Revealing Relationship Status
Credit goes to Facebook’s nifty feature of letting all friends know about the relationship status of each other. All personal and private things are becoming public and a source of appreciation. From relationship status and engagements to break-ups, divorce, and the birth of a child, everything is public. This trend isn’t only common among ordinary people but celebrities, politicians and all famous names also take advantage of it.
So why is everything going public?
Why does everyone seem like they overshare their lives on social media? We look into this new trend that seems to be more common.
Is oversharing the new ‘trend’?
According to the author of Chaos: In Romance, Sexuality, and Fidelity, Raksha Bharadia, the dynamics of love and relationships are completely different from the past. Social media platforms have altered the way people used to protect their relationships, a few years ago.
Today, people feel the need to relate to others. Whether it’s their financial health, relationships, married or student lives. With that being said, they literally cannot resist sharing what is happening in their lives. Another analyst explained that this transition could be the result to maintain a reputation among people.
When you talk about your private lives, it will save you from a lot of issues that might arise otherwise. When celebs or famous people discuss their life happenings on social networks, they keep their connections aware of the truth.
Talking publicly about private lives is a ‘new trend’ that people are adopting, and are quite satisfied with not facing issues afterward.
Loneliness is a pandemic
Loneliness and lack of social associations also lead to an increase in social media usage. Most people feel closer to their virtual friends instead of their real-life ones.
They are more inclined towards them and share personal details more often. Their goal is the same- social acceptance and general liking. Self-clarification about anything and everything is another reason because it enables a person to control perceptions.
Ways to Protect Your Online Life on Social Media

Cover your footprints as default
Strong passwords, installing the latest security updates, and two-factor authentication are the key to maintaining good security hygiene. Here, the key is to understand the difference between security and privacy. The latter refers to keeping your activities, actions, and movements safe from tracking by surveillance or advertisers. Whereas, security means to keep your stuff safe from others’ access- like hacking your account or stealing credit card numbers. To maintain your private life on the internet, you have to pay attention to both and do the three things as mentioned.
There’s fish in those Social Network..
All attacks on your online life are not necessarily from hackers or malware. Sometimes, it’s because of mishandling of your personal details or passwords. Anyone can find passwords either through a phone call, an email, or a text message. You have to search for their authenticity and make sure that the messages are legit. For grammar or spelling errors, email from a weird domain or links of websites other than from where it is coming simply ignores them!
We have a great article to help you work out if you’re talking to a catfish here.
Use Browsers More Than Downloading Apps on Your Phone
Avoid using too many apps in order to protect privacy and maintain security, even from surveillance. Mobile applications have algorithms that help data extractors fetch information. Do you really need to give your correct information to general Apps? give them fake data! and always remove all unnecessary apps and keep your mobile light as much as possible.
Use an Encrypted Messaging App
For safe communication, always go for applications that offer end-to-end encryption like WhatsApp or Signal. This will secure the messages and doesn’t let anyone read them except for the sender and the receiver. However, be mindful that indeed the data is encrypted, but reverse social media tools can still find users by Signal and Whats App, including ours at UserSearch.org.
Following on from that, your metadata is still prone to access which could enable anyone to learn about your personality. Since WhatsApp is under Facebook, whatever contacts and details you share on WhatsApp, Facebook gets those details but cannot access your messages.
If you use an iPhone, encryption is only available for iMessage when the receiver is also an iOS user. An Android user cannot enjoy this facility. On the other hand, Signal provides encryption for both iPhone and Android.
Your personal add preferences (for those that like to see ads!)
Don’t forget to check the settings of apps and social media platforms. Turn off all ad personalization options to restrict companies from conducting invasive tracking. For a Google account, log in to MyActivity and delete everything that is available. Whether they are search terms, YouTube activities, log-in details, etc., don’t leave anything for data extractors that could bring them closer to you.
Climb a mountin, with the first step.
It’s really irritating to control your digital security and privacy these days but, starting with small things at a time can make a huge difference. Not sure where to start? It’s simple- set small and achievable targets and make efforts to get to them before starting with another.
Likewise, you don’t have to list down all accounts for integration into your password manager. Simply, focus on one account and log into it. Do some basic things- strengthen your password, turn on two-factor authentication, and don’t let anyone get access to your account. Once done, it’s now up to you whether to get deeper into more settings or move on to another account for the same steps. And of course, use a reverse lookup tool like ours to check what profiles are actually public. You may find lost and forgotten profiles that you made years ago. They don’t just disappear, you need to delete them!
Read the Privacy Fineprint
Be certain about the privacy policies of every social network or platform before sharing your personal details. If your kids are downloading some apps, instruct them to do the same, and rest assured about maintaining privacy while using the internet.
You’re Home : Wi-Fi and Social Networks
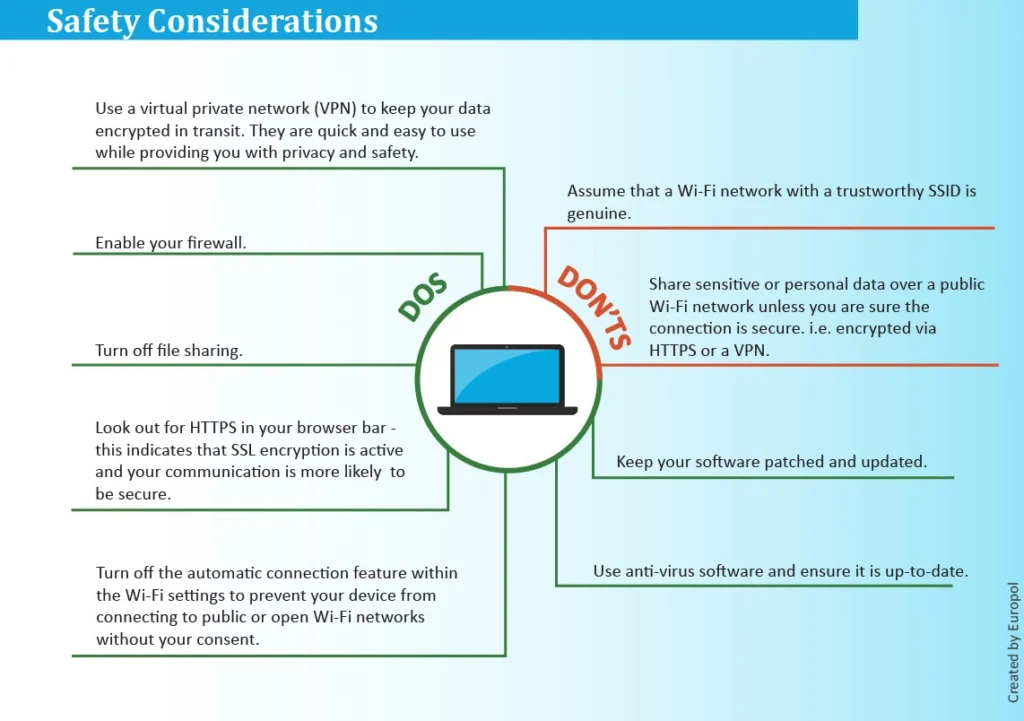
While using your personal Wi-Fi device that has a password, share your details carefully. What if your Wi-Fi device isn’t protected and your neighbors can easily access it? Well, hackers don’t bother if the device is secured with a password or not, they can easily hack your email addresses, passwords, and other data if you transfer it through the Wi-Fi router. Also, some of the older routers have pre-set passwords. Hackers can use these lists found online to brute-force access. Always reset your Wifi password and set MAC rules, to limit who can join. Finally….change the SSID, don’t put your family or business name in there to make it easier for you to find yours!
Did you get all that?
Sorry, perhaps not as exciting as some of our other articles, but just as important.
The Internet has made everything possible. We can order the weekly shop in pajamas, chat to our friend’s hundreds of miles away, even walk through ancient Egypt (google earth). But, let’s not forget our heads. It also allows for invading one’s privacy, letting governmental authorities analyze your data, get scammed, and lose your savings. Data is useful, and also dangerous.
Keep your online footprint private, try not to follow the trend, and keep your eye out for Catfish.
Further Reading
Did you find this article useful? If so, you may want to check out our others:



